Saturday, April 21, 2018
Accessing Publicly Available Information on the Internet Is Not a Crime
According to CBC News (April 16, 2018) a 19-year-old is facing a criminal charge for downloading files from Nova Scotia's freedom-of-information portal. The teen has been charged with "unauthorized use of a computer," which carries a possible 10-year prison sentence, for downloading approximately 7,000 freedom-of-information releases.
The vast majority of these files were already publicly available, and had been redacted prior to release to remove any personal information.
But about 250 of the reports were prepared for Nova Scotians requesting their own government files. These un-redacted records contained sensitive personal information, and were never intended for public release.
These documents were hosted on the government web server that also hosted public records containing no personal information. Every request hosted on the server contained very similar URLs, which differed only in a single document ID number at the end of the URL. The teenager took a known ID number, and then, by modifying the URL, retrieved and stored all of the FOIA documents available on the Nova Scotia FOIA website.
Canadian authorities should drop charges against a 19-year-old Canadian accused of "unauthorized use of a computer service" for downloading thousands of public records hosted and available to all on a government website. The whole episode is an embarrassing overreach that chills the right of access to public records and threatens important security research.
--
It is important to be aware that any information that is posted to a publicly accessible web-site may accessed by the public. Some people may download that information, read it, re-post it, etc. Accessing publically accessible information is not a crime. It is not unauthorized use of a computer, cyber-stalking, hacking, or whatever other foolishness the government wants to charge.
If you don't want the public to access information, don't put it on a public web-site, or at a minimum if you must post it on-line, make sure that it is encrypted and password protected.
Password Generators
In January 2018, I wrote about generating random passwords by using a 6x6 matrix, and by using Dice Ware. These are excellent methods when you don't have access to a computer, but in most cases where we need to generate strong passwords it is because we are going to use them in some type of computer application and thus we have computer access.
If you use a password manager (and you should) it probably has a built-in password generator. However, there are also several password generators on-line that you can use to quickly generate random passwords.
Some of these password generators are listed below (may favorites are Random.Org and Gibson Research).
Random.Org
Gibson Research
Norton Identity Safe
Last Pass
Dashlane
XKPasswd
Privacy Tools
Secure Password Generator
--- Password Strength Checkers ---
Password strength checkers let you estimate the security of various password formats. Never enter you actual password into an on-line password strength checker, rather use them to help understand the strengths and weaknesses of different password schemes.
How Secure is My Password? (Dashlane)
Password Meter
Kaspersky
On-line security tips from Password Generator Net (Secure Password Generator)
To prevent your passwords from being hacked by social engineering, brute force or dictionary attack method, and keep your online accounts safe, you should notice that:
1. Do not use the same password, security question and answer for multiple important accounts.
2. Use a password that has at least 16 characters, use at least one number, one uppercase letter, one lowercase letter and one special symbol.
3. Do not use the names of your families, friends or pets in your passwords.
4. Do not use postcodes, house numbers, phone numbers, birthdates, ID card numbers, social security numbers, and so on in your passwords.
5. Do not use any dictionary word in your passwords.
6. Do not use two or more similar passwords which most of their characters are same, for example, ilovefreshflowersMac, ilovefreshflowersDropBox, since if one of these passwords is stolen, then it means that all of these passwords are stolen.
7. Do not use something that can be cloned ( but you can't change ) as your passwords, such as your fingerprints.
8. Do not let your Web browsers( FireFox, Chrome, Safari, Opera, IE ) to store your passwords, since all passwords saved in Web browsers can be revealed easily.
9. Do not log in to important accounts on the computers of others, or when connected to a public Wi-Fi hotspot, Tor, free VPN or web proxy.
10. Do not send sensitive information online via unencrypted( e.g. HTTP or FTP ) connections, because messages in these connections can be sniffed with very little effort. You should use encrypted connections such as HTTPS, SFTP, FTPS, SMTPS, IPSec whenever possible.
11. When travelling, you can encrypt your Internet connections before they leave your laptop, tablet, mobile phone or router. For example, you can set up a private VPN( with MS-CHAP v2 or stronger protocols ) on your own server( home computer, dedicated server or VPS ) and connect to it.
Alternatively, you can set up an encrypted SSH tunnel between your router and your home computer( or a remote server of your own ) with PuTTY and connect your programs( e.g. FireFox ) to PuTTY.
Then even if somebody captures your data as it is transmitted between your device( e.g. laptop, iPhone, iPad ) and your server with a packet sniffer, they'll won't be able to steal your data and passwords from the encrypted streaming data.
12. How secure is my password? Perhaps you believe that your passwords are very strong, difficult to hack. But if a hacker has stolen your username and the MD5 hash value of your password from a company's server, and the rainbow table of the hacker contains this MD5 hash, then your password will be cracked quickly. To check the strength of your passwords and know whether they're inside the popular rainbow tables, you can convert your passwords to MD5 hashes on a MD5 hash generator, then decrypt your passwords by submitting these hashes to an online MD5 decryption service. For instance, your password is "0123456789A", using the brute-force method, it may take a computer almost one year to crack your password, but if you decrypt it by submitting its MD5 hash( C8E7279CD035B23BB9C0F1F954DFF5B3 ) to a MD5 decryption website, how long will it take to crack it? You can perform the test yourself.
13. It's recommended to change your passwords every 10 weeks.
14. It's recommended that you remember a few master passwords, store other passwords in a plain text file and encrypt this file with 7-Zip, GPG or a disk encryption software such as BitLocker, or manage your passwords with a password management software.
15. Encrypt and backup your passwords to different locations, then if you lost access to your computer or account, you can retrieve your passwords back quickly.
16. Turn on 2-step authentication whenever possible.
17. Do not store your critical passwords in the cloud.
18. Access important websites( e.g. Paypal ) from bookmarks directly, otherwise please check its domain name carefully, it's a good idea to check the popularity of a website with Alexa toolbar to ensure that it's not a phishing site before entering your password.
19. Protect your computer with firewall and antivirus software, block all incoming connections and all unnecessary outgoing connections with the firewall. Download software from reputable sites only, and verify the MD5 / SHA1 / SHA256 checksum or GPG signature of the installation package whenever possible.
20. Keep the operating systems( e.g. Windows 7, Windows 10, Mac OS X, iOS, Linux ) and Web browsers( e.g. FireFox, Chrome, IE, Microsoft Edge ) of your devices( e.g. Windows PC, Mac PC, iPhone, iPad, Android tablet ) up-to-date by installing the latest security update.
21. If there are important files on your computer, and it can be accessed by others, check if there are hardware keyloggers ( e.g. wireless keyboard sniffer ), software keyloggers and hidden cameras when you feel it's necessary.
22. If there are WIFI routers in your home, then it's possible to know the passwords you typed( in your neighbor's house ) by detecting the gestures of your fingers and hands, since the WIFI signal they received will change when you move your fingers and hands. You can use an on-screen keyboard to type your passwords in such cases, it would be more secure if this virtual keyboard( or soft keyboard ) changes layouts every time.
23. Lock your computer and mobile phone when you leave them.
24. Encrypt the entire hard drive with LUKS or similar tools before putting important files on it, and destroy the hard drive of your old devices physically if it's necessary.
25. Access important websites in private or incognito mode, or use one Web browser to access important websites, use another one to access other sites. Or access unimportant websites and install new software inside a virtual machine created with VMware, VirtualBox or Parallels.
26. Use at least 3 different email addresses, use the first one to receive emails from important sites and Apps, such as Paypal and Amazon, use the second one to receive emails from unimportant sites and Apps, use the third one( from a different email provider, such as Outlook and GMail ) to receive your password-reset email when the first one( e.g. Yahoo Mail ) is hacked.
27. Use at least 2 different phone numbers, do NOT tell others the phone number which you use to receive text messages of the verification codes.
28. Do not click the link in an email or SMS message, do not reset your passwords by clicking them, except that you know these messages are not fake.
29. Do not tell your passwords to anybody in the email.
30. It's possible that one of the software or App you downloaded or updated has been modified by hackers, you can avoid this problem by not installing this software or App at the first time, except that it's published to fix security holes. You can use Web based apps instead, which are more secure and portable.
31. Be careful when using online paste tools and screen capture tools, do not let them to upload your passwords to the cloud.
32. If you're a webmaster, do not store the users passwords, security questions and answers as plain text in the database, you should store the salted ( SHA1, SHA256 or SHA512 )hash values of of these strings instead. It's recommended to generate a unique random salt string for each user. In addition, it's a good idea to log the user's device information( e.g. OS version, screen resolution, etc. ) and save the salted hash values of them, then when he/she try to login with the correct password but his/her device information does NOT match the previous saved one, let this user to verify his/her identity by entering another verification code sent via SMS or email.
33. If you are a software developer, you should publish the update package signed with a private key using GnuPG, and verify the signature of it with the public key published previously.
34. To keep your online business safe, you should register a domain name of your own, and set up an email account with this domain name, then you'll not lose your email account and all your contacts, since your can host your mail server anywhere, your email account can't be disabled by the email provider.
35. If an online shopping site only allows to make payment with credit cards, then you should use a virtual credit card instead.
36. Close your web browser when you leave your computer, otherwise the cookies can be intercepted with a small USB device easily, making it possible to bypass two-step verification and log into your account with stolen cookies on other computers.
37. Distrust and remove bad SSL certificates from your Web browser, otherwise you will NOT be able to ensure the confidentiality and integrity of the HTTPS connections which use these certificates.
38. Encrypt the entire system partition, otherwise please disable the pagefile and hibernation functions, since it's possible to find your important documents in the pagefile.sys and hiberfil.sys files.
39. To prevent brute force login attacks to your dedicated servers, VPS servers or cloud servers, you can install an intrusion detection and prevention software such as LFD( Login Failure Daemon ) or Fail2Ban.
Friday, April 20, 2018
Wickr "On Password Protection"
A white paper "On Password Protection" by Joël Alwen, Wickr Cryptography.
This white paper is an excellent overview of password use on the Wickr Me platform. It also provides information on password protection in general. I like Wickr Me as a secure communications platform, and recommend reading this white paper if you also use Wickr.
Counter Extremism Project
The Counter Extremism Project (CEP) is a not-for-profit, non-partisan, international policy organization formed to combat the growing threat from extremist ideologies. Led by a renowned group of former world leaders and diplomats it combats extremism by pressuring financial and material support networks; countering the narrative of extremists and their online recruitment; and advocating for smart laws, policies, and regulations.
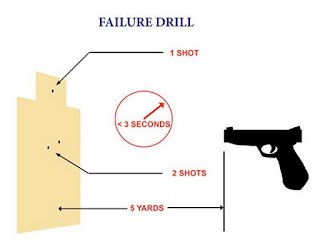
The Failure Drill Revisited
During the Mozambique war of independence, a mercenary named Mike Rousseau had occasion to be jumped by a terrorist at very close range. Rousseau applied two shots from his pistol, I believe it was a Hi Power, to the vital zone of his attacker. The results were not satisfying, as the attacker stayed on his feet and remained a threat. Rousseau then tried for a head shot, instead hitting the bad guy high in the throat and severing the spinal column which ended the encounter.
Sometime afterward, Col. Jeff Cooper heard about the incident and incorporated it into a Gunsite training exercise that he called the Mozambique Drill. For whatever reason, over the years, the exercise has come to be called "The Failure Drill."
So what do you do when an attacker is hopped up on drugs, or wearing body armor and your shots to center of mass are not having the desired effect? This article in the American Rifleman revisits that question.
This YouTube video from Richard Mann demonstrates the Failure Drill.
Active Shooter - Should You Be Armed?
An active shooter is an individual actively engaged in killing or attempting to kill people in a confined and populated area, with no distinctive time period between the shootings. In most cases there is no pattern or method to the active shooter’s selection of victims. Active shooter situations are unpredictable and evolve very quickly.
Studies conducted by the Department of Homeland Security (DHS) found that the average active shooter incident lasts just 12 minutes, with 37% of active shooter incidents lasting less than five minutes. The average time for law enforcement to respond to an active shooter incident was 18 minutes. Forty-three percent of the time an active shooter incident was over before the arrival of law enforcement. When law enforcement arrived while the shooter was still active, he often stopped his attack – turning his attention toward the responding law enforcement officers.
What the available research clearly showed was that during an active shooter incident, the people with the ability to react to and stop an active shooter are the shooter’s potential victims, the people on scene when the active shooter incident begins. Once an active shooter is confronted with an armed response the active shooting incident usually ends. The active shooter may be shot by the armed responder, take his own life (commit suicide), or focus his attack on the armed responder, but in each case that active shooter is no longer randomly murdering the people around him.
The effect of an armed response was seen in December 2013, during an active shooter incident at Arapahoe High School in Centennial, CO. As the shooting began, James Englert, a sheriff’s deputy assigned as the school resource officer, ran toward the sound of the gun fire and confronted the shooter. Once confronted by Deputy Englert the shooter stopped targeting the students around him in the school and took his own life. The time from beginning to end of this active shooter incident was just 80 seconds, because a good guy with a gun was present to stop the bad guy with a gun.
In December 2012, Nick Meli confronted an active shooter in the Clackamas Town Center, near Portland, OR. Meli drew his concealed handgun and aimed it at the active shooter but was unable to get a clear shot off for fear of hitting innocent people running behind the shooter. Meli reported that after the active shooter saw him with his pistol ready to shoot, there was only one more shot fired when the active shooter committed suicide, ending his own life. As with the active shooter incident in Centennial, CO once the active shooter was met with an armed response the incident ended with the criminal killing himself.
In January 2014, an active shooter entered a club in Portland, OR and began shooting customers. The active shooter first shot the club’s security guard, and then shot two other people in the club. Before the active shooter could shoot anyone else an armed private citizen in the club drew his concealed handgun and shot the attacker, ending the incident. This active shooter incident ended without further death or injury because again a good guy with a gun was present to stop the bad guy with a gun.
Colorado State Rep. Carole Murray stated: “Most of the mass killings that we talk about have been affected in gun free zones. So when you have a gun free zone, it’s like saying, come and get me.” John Wills (2013) writing for Officer.Com stated: “the venues selected by the bad guys are often ‘soft targets… gun-free zones,’ where it’s likely the shooter will encounter minimal or no resistance.” Nick Dial (2013) commenting in Law Enforcement Today stated: “The largest disconnect from reality currently responsible for more school shooting victims than any other is the so-called ‘gun free zone.’ The ‘gun free zone’ continues to be pushed as a mainstay for schools. In reality, it does nothing to protect the individual. Instead, such zones bar law-abiding citizens from their fundamental right of defense.” A 2009 Washington Times editorial pointed out that even our military installations are gun free zones, putting our Service Members at risk from active shooters.
Time after time, public murder sprees occur in “gun-free zones” - public places where citizens are not legally able to carry guns. The list is long, including massacres at Virginia Tech and Columbine High School along with many less deadly attacks. Last week’s [November 5, 2009] slaughter at Fort Hood Army base in Texas was no different... terrorists would face more return fire if they attacked a Texas Wal-Mart than the gunman faced at Fort Hood, home of the heavily armed and feared 1st Cavalry Division... [Military personnel are prohibited from carrying a personal firearm on base, even if they possess a state concealed weapons permit.]
Most people understand that guns deter criminals. Research also shows that the presence of more guns limits the damage mass murderers can unleash. A major factor in determining how many people are harmed by these killers is the time that elapses between the launch of an attack and when someone - soldier, civilian or law enforcement - arrives on the scene with a gun to end the attack. All the public shootings in the United States in which more than three people have been killed have occurred in places where concealed handguns have been banned.
Thirteen dead bodies in a Texas morgue are the ultimate fruit of gun-control illogic - in which guns are so feared that government regulation even tries to keep them out of the hands of trained soldiers. (Washington Times 2009)
While available data did not indicate that a gun free zone was a primary factor for active shooters selecting their targets, the fact remains that most active shooter events have occurred in facilities where possession of firearms was prohibited. Gun free zones do nothing whatsoever to prevent violent criminals from attacking you, nor do they in anyway protect you against an active shooter. A criminal bent on murder is not going to be deterred because his target is in a gun free zone. Gun free zones do however ensure that law-abiding individuals will be unarmed and thus defenseless when confronted by an armed violent criminal.
Law enforcement response to an active shooter incident will always be delayed to some extent. No matter how quickly the police arrive, there will be some delay from the time they receive the call until they arrive on scene. During this time the active shooter is free to continue his shooting spree, unless stopped by an armed person at the incident scene. The Sonora, CA Police Department (2013) stated: “Because active shooter incidents are often over within 5-15 minutes, before Law Enforcement arrives on scene, individuals must be prepared both mentally and physically to deal with an active shooter situation.”
If you find yourself in an active shooter situation, your best chance for survival is to flee the area if you can do so without being observed by the shooter. If you are unable to make it to an exit without coming into the shooter’s field of fire, you may be able to temporarily hide from the shooter and thereby avoid being shot, but you must be prepared to move and escape the area as soon as the shooter’s attention is focused elsewhere. However, when you come face-to-face with an armed violent criminal intent on killing you, your only real option for survival is to be armed yourself and trained to use your firearm to defend yourself and those around you.
References
Dial, Nick. (2013). “Gun-free zones: A threat to every child.” Law Enforcement Today. August 4, 2013. http://lawenforcementtoday.com/2013/08/04/gun-free-zones-a-threat-to-every-child/
Follman, Mark. (2013). “Opinion flashback: NRA’s gun-free zone myth.” USA Today. September 18, 2013. http://www.usatoday.com/story/opinion/2013/03/24/nras-gun-free-zone-myth--column/2015657/
Harwood, Matthew. (2012). “Researchers offer new solution to active shooter mitigation.” Security Management. August 10, 2012. http://www.securitymanagement.com/news/researchers-offer-new-solution-active-shooter-mitigation-0010209
Murgado, Amaury. (2013). “Quicker response to active shooters.” Police: The Law Enforcement Magazine. October 16, 2013. http://www.policemag.com/channel/patrol/articles/2013/10/quicker-response-to-active-shooters.aspx
Richardson, Valerie. (2013). “Colo. governor says active-shooter protocol saved lives at school.” The Washington Times. December 15, 2013. http://www.washingtontimes.com/news/2013/dec/15/colo-governor-says-active-shooter-protocol-saved-l/?page=all
Schweit, Katherine W. (2013). “Addressing the problem of the active shooter.” FBI Law Enforcement Bulletin. May 7, 2013. http://www.fbi.gov/stats-services/publications/law-enforcement-bulletin/2013/May/active-shooter
Sernoffsky, Evan. (2014). “Gunman hits 3 before being shot by bystander at Portland club.” KGW News. January 12, 2014 on Northwest Cable News. http://www.nwcn.com/news/oregon/Gunman-hits-3-before-being-shot-by-bystander-at-Portland-strip-club-239845821.html
Sonora, CA Police Department. (2013). “Information on active shooter incidents.” January 4, 2013. http://www.sonorapd.com/information-on-active-shooter-incidents/
Terry, Lynne. (2012). “Clackamas Town Center shooting: Man says he had shooter in his sights, but chose safety over firing.” The Oregonian. December 17, 2012. http://www.oregonlive.com/clackamascounty/index.ssf/2012/12/security_guard_said_he_had_rob.html
Washington Times Editorial. (2009). “End Clinton-era military base gun ban.” The Washington Times. November 11, 2009. http://www.washingtontimes.com/news/2009/nov/11/end-clinton-era-military-base-gun-ban/
Wills, John. (2013). “What we know about active shooters”. Officer.Com March 4, 2013. http://www.officer.com/article/10887915/what-we-know-about-active-shooters
Thursday, April 19, 2018
CryptoCat
Cryptocat is free software with a simple mission: everyone should be able to chat with their friends in privacy.
In an interconnected world where everyone is watching - not just malicious hackers but even the government - privacy and security of your communication is more important than ever.
With Cryptocat, you can rest easy with the knowledge that your messages are secure and encrypted, from sending to receiving.
With Cryptocat, all messages are encrypted by default, and are "Forward Secure," meaning they can't be decrypted even if your keys are stolen. One Cryptocat account across multiple devices will be able to receive your "Forward Secure" messages even when you're offline.
Cryptocat provides users with the ability to share documents, video recordings, photos and other such media.
Cryptocat is cross-platform, available on Windows, Linux, and Mac. Its code is completely open-source and transparent, allowing anyone to review and verify the quality of its security.
- Open source. All Cryptocat software is published transparently.
- Encrypted by default. Every message is encrypted, always.
- Forward secure. Chats are safe even if your keys are stolen.
- Multiple devices. Devices receive messages even when offline.
- File sharing. Securely share files with friends.
To create a Cryptocat account you simply choose a user name (that is not already in use) and a strong password. There is no need to associate your Cryptocat account with an e-mail address or a telephone number.
The Cryptocat's chat server is located in the Bahnhof Bunker, in Sweden.
Nate Cardozo, Attorney with EFF Talks Encryption at RSA Conference 2018
Threatpost’s Tom Spring talks to crypto expert Nate Cardozo, senior staff attorney with the Electronic Frontier Foundation at RSA Conference 2018 about the U.S. government’s current position on device encryption and law enforcement’s use of iPhone passcode cracker called GreyKey. (YouTube Video, 9 minutes)
The CryptoCat is out of the bag!
How Human Behavior and Decision Making Expose Users to Phishing Attacks
Cybercriminals use phishing and social engineering to defeat data and system security by exploiting weaknesses in decision making and human behavior. Approximately 95% of cyber attacks and events involve preventable human error and behavior weakness. This report asserts that cybersecurity behavior relies on decision making, and, therefore, Internet users must be aware of the ways their behaviors and decision making expose them to cyber-threats. (Citizens Crime Commission of NYC)
The Smart Girl's Guide to Privacy
Rise Up has made a PDF (178 pages) copy of The Smart Girl's Guide to Privacy available on their web-site.
The whirlwind of social media, online dating, and mobile apps can make life a dream - or a nightmare. For every trustworthy website, there are countless jerks, bullies, and scam artists who want to harvest your personal information for their own purposes. But you can fight back, right now.
In The Smart Girl’s Guide to Privacy, award-winning author and investigative journalist Violet Blue shows you how women are targeted online and how to keep yourself safe. Blue’s practical, user-friendly advice will teach you how to:
–Delete personal content from websites
–Use website and browser privacy controls effectively
–Recover from and prevent identity theft
–Figure out where the law protects you - and where it doesn’t
–Set up safe online profiles
–Remove yourself from people-finder websites
Even if your privacy has already been compromised, don’t panic. It’s not too late to take control. Let
The Smart Girl’s Guide to Privacy helps you cut through the confusion and start protecting your online life.
If you would like a printed copy of this book, you can buy a copy from Amazon.
Social Engineering: How The Human Factor Puts Your Company At Risk
In a report from Positive Technologies - "Social Engineering: How the Human Factor Puts Your Company At Risk", we read that the firm studied its 10 largest pen testing projects performed for clients in 2016 and 2017. These tests included 3,332 emails sent to employees with links to websites, password entry forms, and attachments, mimicking the work of hackers.
The study found that:
17% of social engineering attacks are successful, and could lead to the compromise of a company's entire corporate infrastructure.
27% of employees clicked an emailed phishing link, making it the most effective method of social engineering. - To make the emails more effective, attackers may combine different methods: a single message may contain a malicious file and a link, which leads to a website containing multiple exploits and a password entry form.
Phishing is a perennial method used by hackers against both common users and corporate infrastructures due to its cheapness, simplicity, and high effectiveness. The best recommendation for common users is to be always on alert. Check who the sender is before clicking a link or opening attachments to make sure that they are not malicious. Before opening a file, scan it with antivirus software. If available at the workplace, open files in a special sandbox. Make sure that the sender’s domain is legitimate. In case of any doubts, use an alternative method to communicate with the sender, such as instant messenger or phone, to check whether an email message and its associated domain are legitimate.
Wednesday, April 18, 2018
myE-Verify
Nearly 600,000 employers at over 1.9 million hiring sites use E-Verify to quickly confirm the employment eligibility of new employees.
Here is what myE-Verify has for you:
Self Check: Verify your personal information against the same records E-Verify checks. Job seekers can confirm that their records are in order or, if a mismatch occurs, learn how to make updates.
Resource Center: Information and learning materials from the worker’s perspective about the E-Verify and employment eligibility verification processes, including your rights, your roles, your employer’s responsibilities and your privacy. Information is in text and video. Many resources are available in multiple languages.
Case Tracker: Track the status of your E-Verify case-in-progress and know if any action is required.
myE-Verify personal accounts: Establish your own secure personal account to access additional
myE-Verify features. Account holders have access to the following two features:
Self Lock: Protect your identity by preventing unauthorized use of your social security number in E-Verify. Self Lock is available to myE-Verify account holders.
Case History: For your security and interest, see where and when your information has been used in E-Verify and Self Check.
** When you sign up for myE-Verify the system will access credit reporting agencies to verify your identity. If you have a security freeze the system will be 'unable to proceed'. This is a good thing as it shows that your personal information is being protected from this type of inquiry, thus limiting your exposure to hackers, data breaches, and identity theft. -- If you haven't locked down your credit reports with a security freeze, at least consider adding a "self lock" to myE-Verify.**
Head of WA State DOL Under Fire for Sharing Information with ICE Officials
According to a KOMO 4 News report (April 17, 2018) - Demonstrators say they feel hurt and deceived by their own government, which they say betrayed the trust of undocumented workers.
They want the DOL director Pat Kohler to quit in the wake of the agency sharing information with the Federal Immigration and Customs Enforcement (ICE), despite an executive order from Governor Jay Inslee telling the state agency to not fully cooperated with ICE unless there's a court order.
The department said it's now re-thinking their protocol in gathering and distributing social security numbers.
According to a report from January of this year, "the Washington state Department of Licensing said it will no longer release personal information to federal immigration authorities without a court order..."
It appears that DOL continued to provide information to ICE without the need for a court order. The question here is whether agencies, such as DOL, should share information collected for one purpose (driver's licensing) with agencies such as ICE for law enforcement purposes in the absence of a court order.
Nobody is saying that we should disregard our immigration laws (well, some may be saying this), rather that in order to collect information about individuals for law enforcement purposes, the police should obtain a warrant our other applicable court order before accessing those records.
Cyber OPSEC Video
Cyber OPSEC (YouTube Video: 43 minutes)
Learn how hackers gain access and how to take basic steps to protect yourself. In this video, a "friendly hacker" and his cohorts will lead you through cyberspace to uncover common mistakes and misgivings as well as the OPSEC measures you can take to protect yourself and your critical information.
Sabotage, Booby-Traps and Direct Action
Among activists and protestors are those who use direct action and sabotage to advance their cause.
From the 1993, Ecodefense: A Field Guide to Monkeywrenching to the more current Earth First Direct Action Manual 3rd Edition there are guides readily available on-line that teach users how to sabotage machinery, damage vehicles, and disrupt commercial operations such a logging, mining, and hunting, as we see in the Earth First Wolf Hunt Sabotage Manual. The March 2017 web-site Earth First! Mechanic's Guild offers updates to Ecodefense.
Awareness of these tactics is important for those who work in these commercial industries, for conservation law enforcement / game wardens working in wilderness areas, and as we see in the Earth-First "Death Manual" for ‘off-roaders’ who ride in wilderness areas. (Note: that the off-road community titled this the "Death Manual", not Earth First.
You don’t have to work in a wilderness area however to be a target of sabotage and direct action, as we can see from the Animal Liberation Front Guide to Direct Action (2010).
Targets of the Animal Liberation Front and Earth Liberation Front can be seen in this table from the May 2013 report An Overview of Bombing and Arson Attacks by Environmental and Animal Rights Extremists in the United States, 1995-2010.
Recipes for Disaster: An Anarchist Cookbook is a 625 page manual discussing a wide range of topics of interest to activists and those interested in direct action. A Step-by-Step Guide to Direct Action provides additional information. In February 2018, I listed other related resources in a blog post Anarchists, Activists, and Saboteurs.
ALF / ELF activists are not the only ones that may pose a safety concern. Marijuana growers frequently set booby-traps to protect their outdoor grow sites. These traps may be fairly simple, like punji pits and cartridge traps, or they may be more complex.
By studying these tactics and techniques we can be safer during any encounter with them.
Tuesday, April 17, 2018
Stop Using 6-Digit iPhone Passcodes
Now that police and Federal agents can allegedly crack iPhones protected with passcodes made of six numbers, it’s time to use longer, harder to guess and crack alphanumeric passphrases.
Cops all over the United States are racing to buy a new and relatively cheap technology called GrayKey to unlock iPhones. GrayShift, the company that develops it, promises to crack any iPhone, regardless of the passcode that’s on it. GrayKey is able to unlock some iPhones in two hours, or three days for phones with six digit passcodes. That’s why security experts are suggesting people stop using passcodes of only six digits altogether. (Motherboard, April 16, 2018)
How to switch to a longer numeric passcode
If a 6-digit numeric passcode isn't secure enough for you, but an alphanumeric password is too much of a hassle, you can set a custom numeric passcode, which simply means more than 6-digits.
Launch Settings from the Home screen.
Tap Touch ID & Passcode.
Enter your existing passcode.
Tap Change Passcode
Re-enter your existing passcode.
Tap Passcode Options.
Tap Custom Numeric Passcode.
Enter your new passcode numbers, as many as you can remember for daily usage.
Re-enter your passcode numbers.
How to switch to a stronger alphanumeric passcode
If the strongest phone access security is what you're after, this is what you'll want to switch to an alphanumeric passcode. The alphanumeric passcode should be long enough that it's extremely difficult to crack with current technology, but not so long that you can't remember it or enter it accurately when you need to. A strong passcode should be 12+ alphanumeric characters.
Launch Settings from the Home screen.
Tap Touch ID & Passcode.
Enter your existing passcode.
Tap Change Passcode
Re-enter your existing passcode.
Tap Passcode Options.
Tap Custom Alphanumeric Code.
Enter your new long, strong alphanumeric password.
Re-enter your new long, strong alphanumeric password.
Signal Messenger Registration Lock
For increased security, you can enable a Registration Lock PIN in Signal. You will be asked to enter this PIN the next time you register your phone number with Signal.Using a Registration Lock PIN adds an additional layer of verification to the registration process that can help prevent someone from using Signal with a phone number that doesn't belong to them.
If you don't already use Signal Private Messenger to secure your private communications, you might be interested in my earlier blog posts:
Signal Private Messenger
Signal Desktop
Harvesting Facebook Photos For A Massive Facial Recognition Database
Forbes (April 16, 2018) has uncovered that over the last five years a secretive surveillance company founded by a former Israeli intelligence officer has been quietly building a massive facial recognition database consisting of faces acquired from the giant social network, YouTube and countless other websites. That database forms the core of a facial recognition service called Face-Int, now owned by Israeli vendor Verint after it snapped up the product's creator, little-known surveillance company Terrogence, in 2017. Both Verint and Terrogence have long been vendors for the U.S. government, providing bleeding-edge spy tech to the NSA, the U.S. Navy and countless other intelligence and security agencies.
Jennifer Lynch, senior staff attorney at the Electronic Frontier Foundation, said that if the facial recognition database had been shared with the US government, it would threaten the free speech and privacy rights of social media users. This could impact the travel and civil rights of tens of thousands of law-abiding travelers who would then have to prove they are not the terrorist or criminal the system has identified them to be.
A YouTube video from 2015 advertises this facial recognition database.
AxCrypt
AxCrypt-2 is one of the world’s most popular encryption programs with over 20 million downloads worldwide. AxCrypt offers both a free version for personal use, and paid Premium and Business editions. The free version uses 128 bit AES encryption, with the option of 256 bit AES encryption in the Premium and Business editions.
AxCrypt is available as an installable program, or as a standalone program that is directly executable - no installation required. I like the standalone version, but others have said they prefer the convenience of the installed version of AxCrypt.
The very first time you launch AcCrypt you must sign in with your email and then enter a confirmation code sent to your email address. You also must create a single master password. Like the master password for your password manager, it needs to be both strong and memorable. This is the password you use to sign in online, and also the password that unlocks the product on your PC.
There are many advanced features available in AxCrypt, making it a useful program for secure file exchange within a team or small group working on a secure project. AxCrypt integrates seamlessly with Windows to compress, encrypt, decrypt, store, send and work with individual files.
The old, legacy version of AxCrypt-1 is available on the Axantum web-site.
AxCrypt-1 was a great program, for file encryption, but lacked the advanced features of AxCrypt-2. While you can still use AxCrypt-1, you should be aware that it is no longer supported.
If you want a simple file encryption program that works like AxCrypt 1, you might consider AESCrypt.
AxCrypt is available as an installable program, or as a standalone program that is directly executable - no installation required. I like the standalone version, but others have said they prefer the convenience of the installed version of AxCrypt.
The very first time you launch AcCrypt you must sign in with your email and then enter a confirmation code sent to your email address. You also must create a single master password. Like the master password for your password manager, it needs to be both strong and memorable. This is the password you use to sign in online, and also the password that unlocks the product on your PC.
There are many advanced features available in AxCrypt, making it a useful program for secure file exchange within a team or small group working on a secure project. AxCrypt integrates seamlessly with Windows to compress, encrypt, decrypt, store, send and work with individual files.
The old, legacy version of AxCrypt-1 is available on the Axantum web-site.
AxCrypt-1 was a great program, for file encryption, but lacked the advanced features of AxCrypt-2. While you can still use AxCrypt-1, you should be aware that it is no longer supported.
If you want a simple file encryption program that works like AxCrypt 1, you might consider AESCrypt.
Monday, April 16, 2018
Graphite - Blockchain-based Software
Do you need a private place to work and collaborate on projects?
Graphite provides a decentralized and encrypted alternative to G-Suite and Microsoft Office. Graphite is blockchain-based software to enable truly private and user-owned personal and business applications for creating, sharing, and communicating.
Graphite lets you create documents and spreadsheets, maintain a contacts list, and have end-to-end encrypted conversations using its messaging service.
In order to use Graphite you will need a Blockstack account.
Blockstack is free for personal use.
Similar to Keybase, Blockstack lets you verify your on-line identity by proving your account on Twitter, Facebook, Github, HackerNews, or providing your Bitcoin address or PGP public key. You may also choose to use Blockstack without providing any identifying information other than an e-mail address.
Graphite is a secure means of collaboration and communication with others, or a way of securely maintaining your documents on-line so that you can access them from anywhere. Because of Graphite's decentralized nature, your documents are safe (as long as you protect your pass-phrase) even if your computer is stolen, lost, seized, or destroyed.
Terror in The Dark
Nikita Malik, the Director of the Centre for the Response to Radicalization and Terrorism, at the UK Henry Jackson Society has published: Terror in The Dark: How Terrorists use Encryption, the Darknet and Cryptocurrencies (April 8, 2018).
Terrorists and extremists are increasingly moving their activities online - and areas of the web have become a safe haven for Islamic State to plot its next attacks, according to a report published today by the Henry Jackson Society.
Terror in The Dark: How Terrorists use Encryption, the Darknet and Cryptocurrencies shows how those planning to commit terrorist atrocities are using extremist networks on the ‘Darknet’ to indoctrinate sympathizers, create a reservoir of propaganda, evade detection and fundraise. It calls for urgent action by government and the policing and security services to step up intelligence gathering and action to counter online extremist activity.
The report shows how terrorists are:
- Using encrypted apps such as Telegram to hide, communicate and plan attacks.
- Drawing interested sympathizers from the ‘surface’ world of the web into the Darknet in order to recruit and indoctrinate new supporters.
- Building up reservoirs of propaganda - saving it from deletion by the security services or tech companies and removing it as potential evidence for use by law enforcement.
- Using cryptocurrencies such as bitcoin to fundraise, taking advantage of the anonymity they offer.
Cops Are The Good Guys
Commentary by Sheriff David Clarke for Prager University
Are cops perfect? Of course not. And no one should expect them to be. But every single day, under the most difficult conditions, the police protect us from the bad guys. In other words, they do their job and they do it well. Former Milwaukee County Sheriff David Clarke makes it very clear: cops are not the problem.
--
Are the Police Racist? - Mentioned in Sheriff Clarke's commentary.
Fentanyl Dangers
Fentanyl is a potent, synthetic opioid analgesic - excellent for controlling serious pain, but also with huge abuse potential. It is 50 to 100 times stronger than morphine.
Fentanyl is a drug that can be severely harmful, or even fatal, with death usually caused by respiratory failure.
Fentanyl-related substances are designed to be absorbed into the body by all means, including injection, oral ingestion, contact with mucous membranes, inhalation, and via transdermal transmission (through the skin). As such, accidental exposure by first responders is a real and potentially deadly danger.
The DEA has a Fentanyl Briefing Guide for First Responders here.
Narcan (Naloxone) may be one way of treating Fentanyl exposure. Does Narcan work on fentanyl since it is an opioid, but it also incredibly potent? While Narcan can work on fentanyl overdoses, these situations often happen extremely quickly, so it can be tough to act quickly enough.
Also, according to the CDC, multiple doses of naloxone may be required following a fentanyl overdose because of how potent it is in comparison to other opioids.
The Surgeon General recommends that more people should carry (and be trained in the use of) Narcan (Naloxone). I believe this is especially true for our first responders.
National Drug & Alcohol IQ Challenge
2018 National Drug & Alcohol IQ Challenge (On-line)
2018 National Drug & Alcohol IQ Challenge (PDF)
Learn more about drugs and drug abuse from the following references and resources:
Drug Guide - A comprehensive and up-to-date source of drug information for parents.
Learn the facts, prevalence and warning signs to help keep your child safe.
Presented by the "Partnership for Drug-Free Kids" In the mid-1980s, when the nation was in the throes of the crack/cocaine epidemic, a small group of advertising professionals discussed how to best use their talents to turn the tide on this issue. They thought, if advertising could be used to sell products, couldn’t it be used to "unsell" them as well? With that, the Partnership for Drug-Free Kids (then known as the Partnership for a Drug-Free America) was born.
Drug Enforcement Administration (DEA) Drug Fact Sheets
You hear about drugs on TV and in the movies, on the radio, in books and magazines, on the Internet, and in daily conversation with friends and peers. Some of the information is accurate, but a lot of it is not. Here are a few realities to consider:
- You can’t predict the effect that a drug can have on you - especially if it’s the first time you try it, and even if it’s a small amount or dose. Everyone's brain and body chemistry are different. Everyone's tolerance for drugs is different.
- Using drugs can lead to abuse, addiction, serious health problems, and even death.
- Drugs that are legal - prescription and over-the counter (OTC) medications - can be just as dangerous as illegal drugs.
Drugs of Abuse - A DEA Resource Guide (2017)
94 pages PDF - Education plays a critical role in preventing substance abuse. Drugs of Abuse, A DEA Resource Guide, is designed to be a reliable resource on the most commonly abused and misused drugs in the United States. This comprehensive guide provides important information about the harms and consequences of drug use by describing a drug’s effects on the body and mind, overdose potential, origin, legal status, and other key facts.
National Drug Threat Assessment (DEA, 2017)
182 pages PDF - The 2017 National Drug Threat Assessment (NDTA) is a comprehensive strategic assessment of the threat posed to the United States by domestic and international drug trafficking and the abuse of illicit drugs. The report combines federal, state, local and tribal law enforcement reporting; public health data; open source reporting; and intelligence from other government agencies to determine which substances and criminal organizations represent the greatest threat to the United States.
National Safety Council - Position on Cannabis (Marijuana) and Driving
Driving under the influence of cannabis1 is an important public safety concern. Smoking, inhaling or eating cannabis with or without alcohol prior to driving is a common practice and increases the risks of driver impairment, motor vehicle crashes and fatalities. It is unsafe to operate a vehicle or other complex equipment while under the influence of cannabis, due to the increased risk of death or injury to the operator and the public.
WebMD - Pill Identifier
Having trouble identifying your pills? Enter the shape, color, or imprint of your prescription or OTC drug. The pill finder will display picture that you can compare to your pill.
Telegram Blocked in Russia 16 April 2018
Russia's state telecommunications regulator said on Monday (April 16, 2018) that it had begun blocking access to messenger service Telegram, implementing a decision by a Russian court from last week.
On Friday, a Moscow court sided with the regulator, Roskomnadzor, in ordering to block Telegram in Russia "immediately." The court ruling follows a Federal Security Services (FSB) demand for Telegram to hand over the "encryption keys" that would allow authorities to read the private conversations of users after the April 2017 St. Petersburg metro terrorist attack.
* Telegram will still work on non-Russian ISP (think VPN here).
It is worth considering the effect that results from a government (any government) being able to block access to a resource on the Internet across an entire country. Of course, this isn't new - China has pretty much complete control of the Internet within its borders - but when a government can shut off the Internet (or access to specific information on the Internet) that can be an issue for human rights and the free exchange of ideas.
Sunday, April 15, 2018
Yahoo and AOL Just Gave Themselves the Right to Read Your E-mails (again)
C|Net (April 13, 2018) reports that Yahoo and AOL just gave themselves the right to read your emails (again). Oath, the media division of Verizon that runs both AOL and Yahoo, is finally unifying the privacy policy of its two giant legacy Internet brands. That means an updated set of privacy terms and policies for hundreds of millions of users. To be clear, Yahoo's previous privacy policy had already stated that Yahoo "analyzes and stores all communications content, including email content," so the company has previously disclosed that it's been able to scan the contents of your emails, at least. (AOL's legacy privacy policy doesn't say anything like that.)
To protect the content of your personal communications it is essential that you encrypt your e-mail. You may choose to use a 'privacy focused' e-mail or encryption service, and/or you may choose to use a method (such as GnuPG / PGP - Pretty Good Privacy) to encrypt the content of your e-mail before you send it. Regardless of what encryption method you choose, if you don't encrypt your e-mail it can be read by anyone.
Dealing With The Police
Law enforcement officers play an important role in our criminal justice system. We rely on the police to keep our communities safe, and to treat us fairly regardless of race, ethnicity, national origin, gender, or residence. The police have a difficult job, a job that most of them - perhaps the vast majority of them - do very well, day after day.
In addition to local police departments and county sheriff's deputies, there are other law enforcement agencies that you might come into contact with, such as the FBI, ICE, or even agents of the Joint Terrorism Task Force (JTTF). Like our local law enforcement agencies, the agents of these Federal agencies are in almost all cases going to act professionally in any contact that you may have with them.
But, "most", "the vast majority", and "almost all", means that there is some small percentage of police officers, Federal agents, and government employees who are going to act inappropriately, or perhaps even criminally.
In any contact with the police it is important to know and retain your rights. As the US Supreme Court said in the 2001 case Ohio v. Reiner, the U.S.; retaining / invoking your rights serves to protect the innocent who otherwise might be ensnared by ambiguous circumstances.
But, what are those rights and how do you go about retaining your rights during contact with the police or some other government agent? Part of this comes from understanding the Constitution and the proper function of government.
Each day during the first week of April 2018, I posted a link to an on-line course that provided some insight into the United States Constitution and the proper function of government. While many readers enjoyed these courses, I was also asked for more specific information and resources for dealing with a police encounter. Unlike finding resources to study the Constitution, finding resources that explain how to act when contacted by police is a bit more problematic.
Too often on-line resources that describe how to act during a police contact are just plain wrong as we see sometimes in the "sovereign citizen" community, or are at best inappropriate as we see with groups like Cop Block.
As with my blog post, Should You Take a Field Sobriety Test? - I think it is important to see what practicing attorneys and civil rights organizations, such as the ACLU, recommend. The following resources give what I believe is appropriate, and sensible advice on how to act when contacted by the police or by a government agent:
In any interaction with the police you have both rights and responsibilities. The following points from the ACLU sums up those rights and responsibilities:
Your Rights
- You have the right to remain silent. If you wish to exercise that right, say so out loud.
- You have the right to refuse to consent to a search of yourself, your car or your home.
- If you are not under arrest, you have the right to calmly leave.
- You have the right to a lawyer if you are arrested. Ask for one immediately.
Your Responsibilities
- Do stay calm and be polite.
- Do not interfere with or obstruct the police.
- Do not lie or give false documents.
- Do remember the details of the encounter.
- Do file a written complaint or call your local ACLU if you feel your rights have been violated.
Subscribe to:
Comments (Atom)